Resource Hub
FEATURED
SPI 360 bridges cybersecurity strategy and execution by automating performance tracking, accountability, and business impact measurement. It moves beyond static assessments, delivering real-time intelligence that enhances decision-making, optimizes investments, and aligns cybersecurity with financial and operational goals...
The CISO Playbook provides a strategic guide to evaluating the SPI framework, enabling CISOs to align cybersecurity initiatives with business objectives, measure true ROI, and confidently communicate cybersecurity's strategic value to stakeholders and boards through AI-powered analysis and financial discipline...
PODCASTS
Metrics don’t just measure performance—they shape it; used carelessly, they can destroy it...
The Strategy Layer Live is an audio project by Tout Media that helps CISOs and cybersecurity leaders rise above operational noise to drive business value through smarter strategy, better alignment, and leadership that lasts...
Candid CISO Season 2 dives into the evolving role of security leaders—navigating AI, boardroom battles, burnout, and business impact. Unfiltered insights, sharp humor, and real talk for CISOs charting their path in 2025’s high-stakes landscape...
CISOs aren’t being eliminated — but they are being quietly redefined, compressed, and sidelined...
How to lead like a next-gen CISO—pragmatic wisdom from Andy Ellis...
Cyber leadership is shifting — and the gulf between yesterday’s CISO and tomorrow’s is only growing...
BLOG
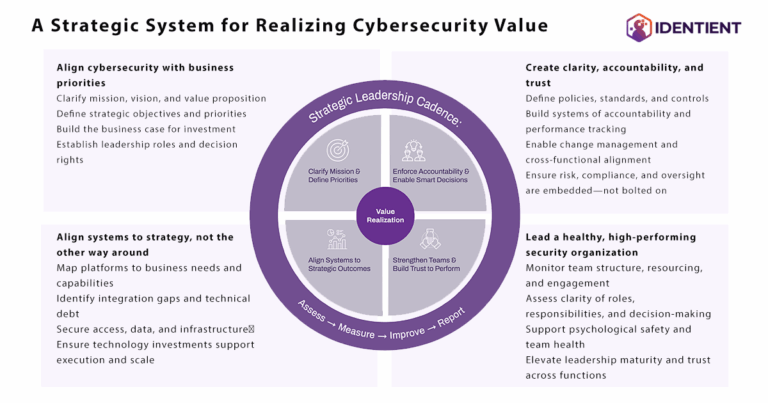
Infographic: Discover SPI 360, a strategic leadership system for CISOs to align cybersecurity with business outcomes, enforce governance, optimize tech, and build resilient teams...
CISO mind maps are helpful, but they reinforce a tactical view of security. Learn why modern CISOs need a new mental model focused on strategy, value, and board-level impact...
Compliance isn’t enough. Learn why CIOs & CISOs must lead with AI-driven Strategic Performance Intelligence to enhance security, governance, and resilience...